There’s been a lot of talk about security, passwords, and authentication. As we put more about us online, our passwords become ever so important. Everything from banking to commerce, friendships to resumes, and even our day jobs require passwords.
Passwords are broken
Having worked in information technology auditing, I can tell you that people hate passwords. If I had so many to remember and they were all necessary for me to get my job done, I would simply pick one, easy-to-remember password. Unfortunately, businesses believe this is unsafe and force users to follow silly rules (8 characters, 2 must be numeric, and you must change this password every 60 days). Due to these rules, things become less secure. Two examples:
- Passwords start showing up on sticky notes next to computers. Or they are all written down in a handy notebook right next to the computer (typically open to the most frequently-used password). Now that “easy to remember” to me password in my head, is now written down and easy to access by anyone.
- Similarly, we use a database like 1Password or some other encrypted database to store all these fancy, super-secure passwords. But, then we protect them behind a single, “easy to remember” password. Now it only takes one password to unlock all your passwords, and we’re right back at square one.
Alex and I feel strongly about password security and he’s written about it many times. Here’s my thoughts and what I’ve found works best for me.
SuperGenPass
Very similar to PwdHash, SuperGenPass creates a unique, complex, secure password for every site you use. The steps are simple:
- Enter a “master password” (eg: puppies)
- Hash that password against the current domain (eg: facebook.com)
- Generate a secure string using those two inputs (eg: 4ced9d6f52dc88d02028d34a3625e43d)
- Truncate the result to X characters (eg: 10)
Here’s how SuperGenPass describes itself:
Instead of storing your passwords on your hard disk or online—where they are vulnerable to theft and data loss—SuperGenPass uses a hash algorithm to transform a master password into unique, complex passwords for the Web sites you visit.
Arguably, the concept of a “master password” means you have one “easy to remember” password that anyone can get to and then use to generate your secure passwords. But, there are a few counterpoints:
- An attacker would need to know I use SuperGenPass (whoops)
- They would need to know how long my generated results are (8, 10, 20 characters long?)
- I use a secure master password which is unguessable and not something I’d write down or use elsewhere
Now that we’re all convinced (right?), the mechanisms of using a password hashing utility are super simple.
- Browse to site
- Type in master password
- Use Bookmarklet or Mobile site to generate hashed password
- Login!
Since I use Safari, I have SuperGenPass added to my Bookmarks Bar and I can use Command + 1 on any page to trigger the bookmarklet to enter my password. It then finds any “password” fields on the page and auto-populates them with the hashed version. This is very fast and hardly any more intrusive than simply typing a password into a form.
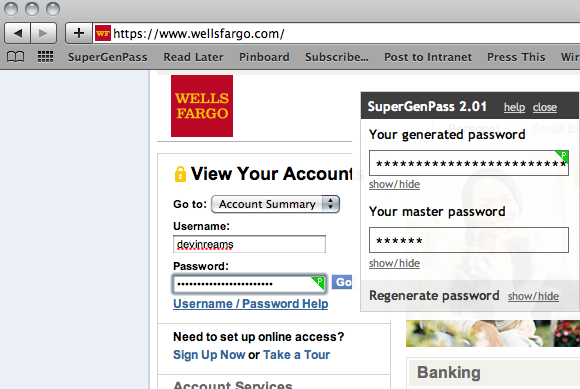
Simply entering my password into the form and hitting Command - 1 means a super-secure password is instantly replaced.
This also works well for me because I can use the Bookmarklet in Mobile Safari (iPhone, iPad). I can pull up the mobile site on any machine in the world. If it’s unavailable? No problem, I’ve stored the mobile site in my Dropbox. Since all that’s needed is JavaScript to run, I can even generate my passwords offline.
Still not convinced? Drop a line or leave a comment to share your thoughts…
Good read. I might end up doing this (or imploring my wife to do it). I switched to a 100% strength password (according to http://www.passwordmeter.com/) in January and find that it isn’t that big of a deal to type for 3 seconds rather than 1 second.
Pingback: Tweets that mention Why I secure my passwords with SuperGenPass — Devin Reams Blog -- Topsy.com
I’ve used SuperGenPass for years and I love it. However, since its security vulnerabilities were first pointed out to me I’ve increasingly tended toward using the mobile version and manually copying my passwords over.
Unfortunately, this significantly less convenient than the UX that SuperGenPass proper offers. What we need is an update that addresses the security vulnerabilities identified by Borklund while still providing the conveniences that make SGP so attractive in the first place.
I hadn’t seen the security vulnerabilities but it makes good sense to take caution with the bookmarklet. Luckily most of the time my password is saved on my computer and the rest of the time I’m copy/pasting on an iOS device. If you’re even more hesitant you could also run the JS or even the mobile site locally to make sure you’re not transmitting anything. Thanks for the comment…
Ironically enough, hard-coding the password into the bookmarklet is a way around the demonstrated vulnerability.
Clever! I hadn’t considered that.
After submitting that last comment, I discovered that there are Chrome extensions for SGP. Now these do have the potential to address that security vulnerability. Best of both worlds?